Articles
- Intel
- Samsung
- Texas Instruments
- STMicroelectronics
- Infineon
- NXP Semiconductors
- Microchip
- Analog Devices
- onsemi
- Skyworks Solutions
- Avago
- Marvell
- Omnivision Technologies
- ROHM
- Seoul Semiconductor
- Silego
- Cirrus Logic
- Silicon Labs
- Lattice Semiconductor
- Cypress Semiconductor
- Toshiba
- Mitsubishi
- Panasonic
- Sharp
- Omnetics
- Laird
- TDK-Lambda
- WAGO
- All Distributors
Electromagnetic Side-Channel Attacks on Cryptographic Systems
Electromagnetic (EM) attacks stand out as particularly powerful. In this article, we will delve into the mechanics of EM attacks, exploring how they function and examining specific types of power attacks that have historically compromised cryptography.
What Are EM Attacks and Why Are They Powerful?
An EM side-channel attack exploits the electromagnetic emissions from an electronic device, serving as a means of information leakage (see Figure 1). These attacks have been extensively researched for decades, making them some of the most well-understood and formidable hardware attacks. Their unique features grant them considerable power compared to other forms of side-channel attacks.
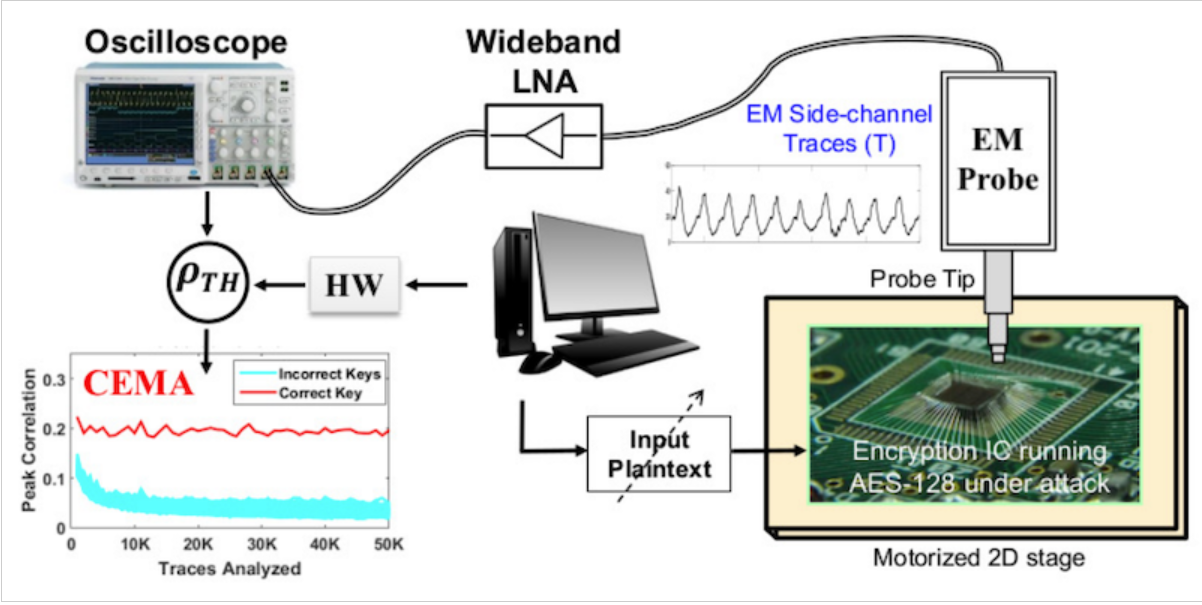
Figure 1. Example setup for an EM-based attack.
EM Attacks Are Non-Invasive
A key aspect of EM attacks is their non-invasive nature, allowing attackers to conduct them without physical access to the targeted device. This ease of execution is a major strength; the attacker simply needs a near-field probe and an oscilloscope. Moreover, EM attacks do not require any modifications to the device, unlike many power-based attacks that demand specialized tools or IC decapsulation.
EM Attacks Are Difficult to Detect
The non-invasive characteristic of EM attacks also means that victims are almost entirely unaware they have been compromised. This enhances the potency of EM attacks, as they are challenging to identify and thwart.
EM Attacks Enhance Data Collection
Additionally, EM-based attacks typically provide data with a higher signal-to-noise ratio (SNR) than power attacks. This leads to a requirement for less signal collection to effectively filter out noise.
How EM Attacks Work
According to Faraday’s Law, electric currents generate magnetic fields. An EM-based side-channel attack leverages this principle by monitoring the EM radiation emitted during a device's operation to extract information. As shown conceptually in Figure 2, attackers physically measure the electromagnetic emissions and employ analytical methods and leakage models to recover sensitive data.
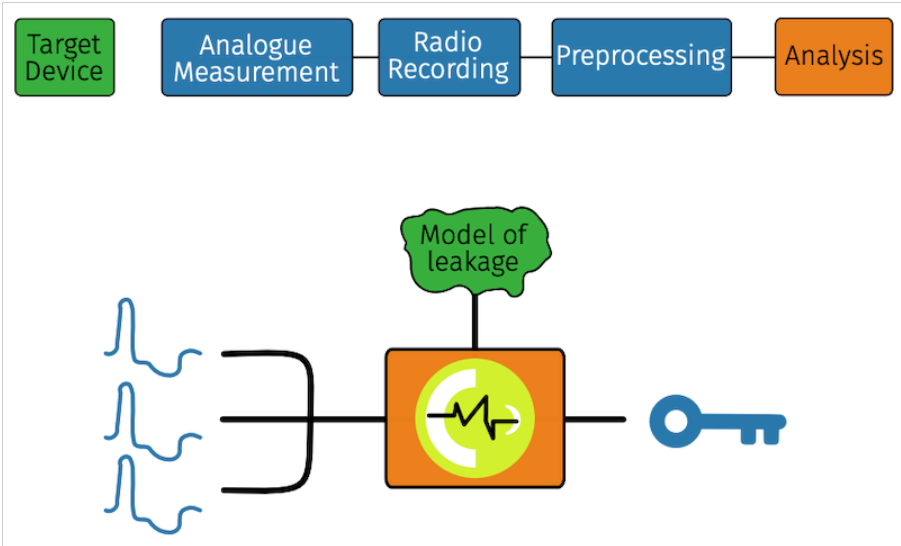
Figure 2. EM-based attacks are used to extract information from the data.
In CMOS devices, current flow primarily occurs during logic state changes at clock edges. These changes are directly tied to binary data streams, indicating a deterministic relationship between EM emissions in a CMOS device and the data being processed. The essence of an EM attack lies in exploiting this relationship to steal information. Attackers can capture these signals using an EM probe tuned to the device's fundamental frequency and its harmonics, followed by applying various statistical techniques and leakage models to extract sensitive information (see Figure 3).
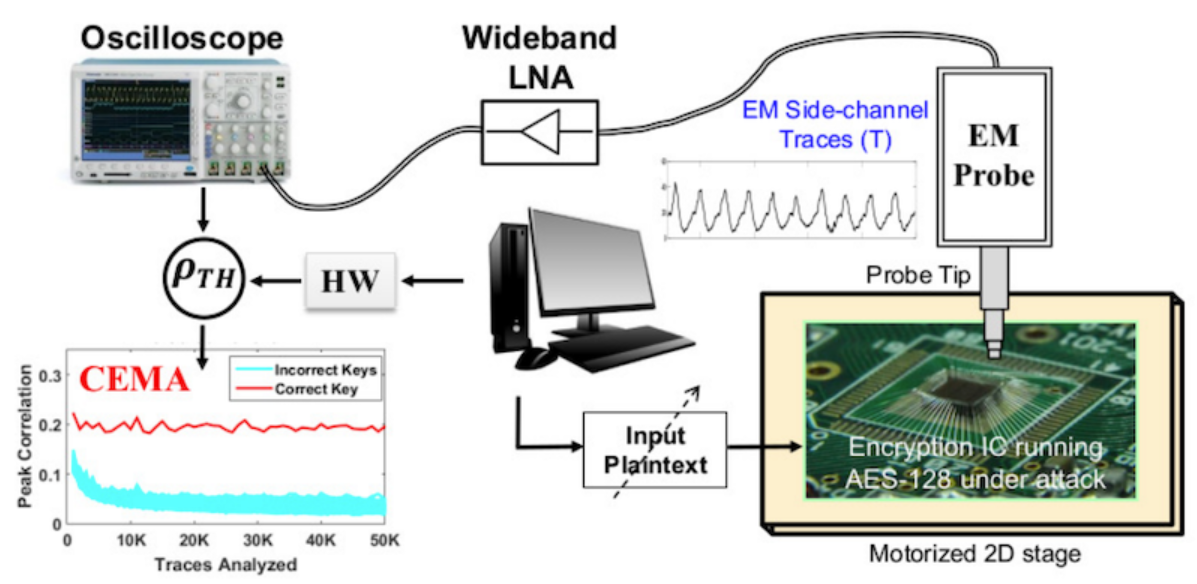
Figure 3. Example setup for an EM-based attack.
Types of EM Side-Channel Attacks
Similar to power attacks, EM attacks can be categorized into two main types: Simple Electromagnetic Analysis (SEMA) and Differential Electromagnetic Analysis (DEMA). The key difference is that SEMA involves interpreting data traces directly, while DEMA entails collecting numerous traces and applying differential statistical methods to reveal data-dependent correlations. Although DEMA attacks are more robust and widely applicable, they tend to be more complex and time-consuming. Recently, the use of machine learning for pattern recognition and classification in analysis has gained traction as these technologies become more sophisticated and accessible.
EM attacks have demonstrated their capability to extract sensitive information from various cryptographic devices. For instance, Fox IT successfully executed an EM attack to compromise an AES-256 core in just five minutes from a distance of one meter. Further research, such as that by Syakkara et al. in their paper titled Leveraging Electromagnetic Side-Channel Analysis for the Investigation of IoT Devices, has shown how EM attacks can non-invasively identify the cryptographic algorithm, software, and firmware version running on IoT devices.
Electronic Devices Vulnerable to EM Attacks
Another factor contributing to the strength of EM attacks is the wide array of electronic devices they can impact. Vulnerable devices include smart cards, mobile payment systems, embedded devices, smartphones, IoT devices, and system-on-chips (SoCs). This list is not exhaustive, yet it highlights that nearly all electronic devices we interact with daily are at risk from EM attacks.
EM Attack Takeaways
This exploration into EM attacks underscores their significant threat potential, especially when combined with tools like machine learning. If devices are not adequately fortified against such vulnerabilities, EM attacks can pose substantial risks to electronic security.
Previous: Power Dissipation of a CMOS Inverte
Next: An Introduction to RISC-V—Understanding RISC’s Open ISA

